|
|
|
|
Part I - Motives for Mind Control | Part II - Resisting the Mind Control State | Part III - Mental Firewalls
Allen Barker, Feb 17, 2002 This is the third of a three-part series of essays on mind control. As the earlier essays explained, "mind control" is the term commonly and historically used to describe clandestine operations to alter human behavior and thought. The series focuses mainly on high-technology techniques involving, for example, surveillance devices and electromagnetic weapons -- though victims of all sorts of mind control techniques have common experiences and sequelae. The first essay of the series, "Motives for Mind Control," dealt with some of the reasons that mind control harassment, torture, and exploitation happens and why it continues. The second part, "Resisting the Mind Control State," dealt with ways to protest and resist mind control abuses in a supposedly "free" society. In this final part, I explore some of the methods and techniques that victims have developed to help them resist these ongoing human rights atrocities committed every day against their bodies and minds. In a sense we are going to have a look at mind control torture from the torture victim's point of view, from "inside" the mind of the victim. This essay is written from the point of view of someone experiencing real torture from externally induced mind control phenomena, including induced voices in the head, surveillance, harassment from various sources, and nonlethal aversive jolts. While I make no secret of the fact that I have personally been subjected to a similar sort of mind control torture, this is not my story. Of course it is influenced by events I have experienced, but the essay is a composite from my interactions with many mind control victims (and provocateurs) over the past few years. I will save the actual details of my own experiences for my lawyers or for prosecutors when that time comes, or perhaps for other writings I might choose to make public. Thus, in keeping with the earlier parts of the series, you do not even have to believe me about my having been tortured -- though it all happened. There are many people in the world, including many American citizens, who have experienced very similar things. You can even think that all of those people made it all up, and still have to be concerned despite your Holocaust denial. The technology undoubtedly exists right now to carry out the sorts of torture operations described in this essay, and will only become more advanced with time. I cover a lot of different techniques and possibilities in this essay, but keep in mind that the truth is bad enough. What we already know and can document is bad enough, and is only the tip of the iceberg. In the spirit of mentioning all the possibilities, though, let me briefly discuss mental illness here. There truly are some people with mental illnesses which occur naturally. There are also people with mental illnesses which were externally and purposely inflicted, for example by harassment operations. And there are mind control victims who are completely normal except that they have undergone years and years of some of the most hideous torture imaginable -- in a lying, despicable society that denies it, ignores it, and further tortures the victims. We know this from documented sources; what the government has admitted is bad enough. I hope this essay will prove helpful even to victims who suffer from true mental illness. I call them victims also because the cowardly U.S. government has hidden behind the skirts of the mentally ill to commit some of the worst atrocities imaginable, and the truly mentally ill are victimized by this as well. The mentally ill are also known to have been used as guinea pigs in mind control experiments precisely because they would tend to be disbelieved and are relatively powerless victims for torturers to experiment on. Some victims may have been poisoned by drugs engineered to cause them psychological problems -- and I do not mean ordinary street drugs. Others have had psychosurgery, microwave harassment, etc., which can cause organic problems in addition to psychological problems. And of course, the mind is really not separate from the body and psychological torture is just as bad as direct physical torture. Most people are still free to think what they want -- to the extent that that still means anything -- and some will try to second guess the victims and provide armchair diagnoses of the victims' problems. People who try to dismiss true torture victims as just mentally ill will receive and deserve the utmost contempt from the victims and from those decent people who know what is really going on. And we will remember. For the reasons described in Part II, the psychiatric and psychological "communities" cannot be trusted, except for a few actual healers here and there. Much of this essay contains a sort of analysis that it is fashionable among the pseudo-intelligentsia to dismiss as just black-and-white thinking. These people have their sixth-grade epiphany that not everything is black-and-white, and for the rest of their lives go around justifying anything convenient with this amoral relativism. They never realize (or it just does not suit their lies) that while nothing is black-and-white, some things are close enough that they might as well be. I will be writing about Nazi pigs, and I mean this in the sense of "Mengele the Nazi pig," not any other cultural pig association. Those who dismiss this sort of thinking perhaps would think differently if they had ever experienced real torture or were capable of the slightest bit of empathy. There is no doubt that this sort of thinking has been misused and misapplied at various times, but I cannot worry about how every moron might misunderstand or misapply what I write. People may well misapply things I have written here, or use them to create some propaganda distraction from what I am actually writing about, but I am describing it the way it is. If you don't call a Nazi a Nazi you end up with Nazism by some other name. Every victim has had to develop his or her own method of coping with the torture. I am not trying to impose my methods on anyone. A religious person under torture finds strength in his or her religion, so some Zen Buddhist philosophy may necessarily be apparent in my writing. In the ignorant U.S. there are still people who will blame a victim for being Buddhist, a major world religion. Of course Mengele the pig tries to justify and rationalize his acts of torture in any and all ways possible. There are the usual myriad ways of blaming and smearing the victims and rationalizing away the acts of the torturer. I hope that this essay will help some victims. I know that I have benefited from the work of other victims who had the courage to speak out about their experiences. Much of this essay deals with the mental "game" of mind control, which is of course not a game at all to the torture victims. You can compare it to having to face mock executions each day. There is also the physical intimidation many victims experience. As a victim might put it, if it is all in my head then who harassed me on the highway? Why did my mail all arrive opened? Why did my phone regularly ring twice a day with hang-up calls? Why did many of my internet posts stop propagating anywhere? Why did a police car pull up beside mine every time I talked about China, on the drive to my honeymoon? The unfortunate reality is that the victims have to develop their own methods to deal with the constant, credible physical threats of death or worse. I wish I could help there, but I do what I can. This is a barbaric and savage nation. What is a Firewall?For the purposes of this essay, let me digress a bit here and describe the concept of a firewall. A firewall, in the historical sense, is a wall built between connected buildings and specifically constructed so that a fire in one unit of the structure will not spread to the other units. In a more recent sense, a firewall is a device on a computer network that keeps nodes of the network separated, for instance so that a hacker attack on one node of the network cannot spread to connected nodes of the network.For our purposes, we can consider all the computers on a network to be like houses on a street. (Network engineers, please bear with me.) Each house has several doors into it, which correspond to what are called ports on a networked computer. A computer actually has thousands of ports, but the principle is illustrated by considering a house with several doors. All the houses have inhabitants in them, who send out messengers to the other houses: But some houses send out the equivalent of burglars also. When the inhabitants of one house want to communicate with the inhabitants of another, they send a messenger to a particular door of the house they want to communicate with. The messenger knocks on the door. Now, the inhabitants of the house can either open the door and let the messenger in or ignore the knock. If they let the messenger in, they can restrict what he is allowed to do while in the house. The messenger may, for example, pick up a piece of paper and carry it back to his house. This would correspond to a file transfer over a network. If the inhabitants of the house accidentally leave a door open, though, a messenger may be able to come in the house without permission and do whatever they like, again without permission. (There are many doors because a messenger occupies a particular door the whole time he is "in the house.") A firewall, in this analogy, would correspond to a complete facade built around a house (or group of houses, to be picky). The actual house is not even visible from the street. The doors of the original house are only visible to messengers if the inhabitants of the house build corresponding doors in the facade. To enter the house in this scenario, a messenger would have to first knock at some visible door of the facade, be allowed in, and then knock at and be allowed into the actual door of the house. In this way the security of the house is greatly increased from unwanted intrusions. (And you can have a collection of trusted houses "inside the fort" which are less protected from each other.) The title of this essay, "Mental Firewalls," comes from an article by Timothy L. Thomas which appeared in the Army War College journal Parameters in Spring 1998. It was titled "The Mind Has No Firewalls." The Army has an often honorable tradition going back to the Revolutionary War, the minutemen, and so forth. But it also has had and still has some treason in its ranks. This is just the "ground truth," the "facts on the ground." An army that tortures the domestic population is an occupation army. Treasonous Nazi pigs, in this real sense rather than some spin machine crap or some pathological liar's bullshit, must be dealt with accordingly. This holds for all branches of the military. This holds for law enforcement as well. It holds for all intelligence agencies also. It holds even when they pretend the torture devices "don't exist." Even if the victim does not realize what is happening to him or her, it is still torture. Informed consent must be truly informed. Torturing an American citizen is at least as treasonous as selling the nation's top secrets to a foreign power. Thomas' article was in fact entered into evidence as part of a lawsuit by Harlan Girard of the International Committee for the Convention Against Offensive Microwave Weapons. The article's central metaphor is that human beings are like the computers on a network, except that they do not have the ability to control the information traffic entering and leaving them. Their ports, or doors, are wide open. This sort of analogy was prevalent during the military "information warfare" buzzword phase, and illustrates the sort of thinking that was going on at the time. [On a note of caution, not all of Thomas' article should be taken literally; whether purposefully or not there is some likely disinfo there.] Deception Operations Against the Human "Biocomputer"What is it that corresponds to your reality? What do you perceive, and how do you make your decisions? You receive information through your eyes, ears, and other senses. You read the information from the writers you choose to read, and listen to the speakers you have access to -- very often these days from TV, radio, or the internet. You think to yourself, in your private inner voice. You visualize and imagine. In information warfare against individuals all of these are thought of as nothing but information channels that can be blocked, censored, co-opted, faked, forged, impersonated, or otherwise controlled to manipulate an individual. If you can control all the information an individual receives then you can control their whole perceived reality. Like the hypnotized subject who does something which violates his ethics while being persuaded to imagine he is doing something else entirely, the information warfare subject is acting in a fantasy world created precisely to manipulate him to do what his controllers want. This is known as a deception operation.Such complete control, as far as I know, is not yet possible, but the principles still hold for whatever approximation can be achieved. And the principles have been put into practice. Of course "information warfare" is a buzzword and most of it is just a take on the ages-old practices of propaganda, lying, and manipulation. But a new buzzword generates funding, and perhaps more importantly serves to morally distance the new "clean" practices from the dirty, filthy business of amorally manipulating human beings like pawns, with complete disregard for unalienable human rights. What was new at the time of information warfare was 1) the internet as a widespread societal force, and 2) the wider development of neuroinfluencing and so-called nonlethal weapons that can directly influence people's brains. As medicine and technology develop ever more advanced prosthetic devices, people will increasingly become cyborgs -- as is already happening. Because of this trend these issues will become increasingly clear with time. That is, it will become increasingly common to have computer devices implanted in one's body. If someone hacks into your home computer and steals or manipulates your data then a crime has been committed and you should rightly be angry. But if someone hacks into your physical body, brain, and mind the violation is incomparably greater. The Basic Modern Mind Control Torture OperationIn this section I will describe the basic torture setup used against our hypothetical, composite mind control torture victim. The focus is on the effects that the victim experiences, not necessarily the particular technology that is used to inflict it. Remember in all of this that the torture any individual receives can vary. It will vary according to the torturers' motives and technology, but will also be tailored to the psychology of the victim. What might bother one person would not bother another. The "professional" torturers will start according to how their torture manuals say to go about torturing someone with your profile, but almost all torturers will refine the torture to the individual if they can. As they learn what bothers you they can focus on that more and more in their torture. As you read this, keep that in mind. These torturers are not any different from the sort you might read about in Red Cross literature, who shock the genitals of victims, etc., except that they have access to abuse the most advanced technology and hide behind an evil U.S. government which sinks to the lowest common denominator of the torturers it protects.First of all, the victim is under constant surveillance. The victim is harassed overtly and covertly, on the street, on internet, etc. All forms of taunting and goading tend to occur. For example, there is a "Marco Polo" type of "can you catch me" taunting. Any and all sorts of high-tech and low-tech harassment are used. (Just because it is sophomoric or pathetic does not mean they will not do it. In fact, this increases the likelihood that the victims will be ridiculed if they complain. Remember the shoe powder to make Castro's beard fall out?) The victim soon has to wonder about everything that breaks or goes wrong in their lives. The harassers use their surveillance to see what troubles the victim is having and then try to "take credit" for causing them. The torturers are often arrogant and even incompetent at their vile torture "jobs" despite using the most advanced technology to commit treason. The victim is purposely isolated. People close to them are threatened or deceptions are created to make the victim suspect those closest to him or her. Deceptions are launched so victims will blame innocent neighbors for the harassment. (Unfortunately, in the despicable circles of mind control torture, it sometimes is a neighbor or even a close family member that truly is responsible. There might be an out-of-control "safe house" next door, for example.) The victim is zapped inside his or her home (or a deception operation is launched so the victim thinks this is what is happening). Heart rhythm palpitations induced by remote technology can cause terror to an individual inside his or her home. The victim's mind is under assault with voice projection, voice cloning. The Village Voice, in an article from July 2001 titled "Psycho Warfare," described an Air Force report uncovered by Nick Begich. Quoting from the article, ...the technology may be able to create high-fidelity speech in humans, "raising the possibility of covert suggestion and psychological direction." It may be possible to "talk" to selected adversaries "in a fashion that would be most disturbing to them." This is exactly what they do, and there are several different technologies documented in the open literature which can achieve this. Some victims may be test cases for such psychological harassment techniques, or the method may already be "perfected" and in covert operational use. [They don't mention this in psych textbooks or in movies about "schizophrenics," do they?]Twenty-four hours a day, the victim is subjected to commands, ridicule, and distractions inside his or her private mind. How would it feel if you heard a voice in your head asking, "Can you hear this?" as if someone were calibrating a torture device? The brain wants to respond; it was never meant to be violated in these ways. Interrogation. What might bother you? Any secrets, etc., the pigs might tease out and harass you with? Anything that would insult you they could focus on? Anything that might distract you they could keep you distracted with? Finally, the victims' supposedly private, subvocalized thoughts are somehow read, or inferred and analyzed. There are various levels at which this can occur, from remote heartbeat and eye gaze analysis all the way up to brain implants telemetering EEG signals. Not all victims report this level of surveillance, and certainly just the other harassment techniques mentioned above result in a grotesque human rights abuse. But many victims discover that even their supposedly private thoughts are being violated and manipulated. Living with Constant HarassmentHow do you deal with "ordinary" social interactions with the pigs harassing you constantly in your mind? Do you act "ethically" and warn everyone you interact with that their privacy is also being invaded, by way of you, against your consent? People you interact with either believe you or they don't, but either way the social dynamic is completely changed. The pigs invade the privacy of everyone around you, by using you, even that of your spouse and children. They may also impersonate anyone you see, in your mind, to make it seem as if that person is the one "contacting" you. They try to make it seem like everyone can hear your private thoughts, that you are "broadcasting" to everyone. (Of course some victims might actually be doing that; if they can read your thoughts they could then broadcast them wide-field or local-field...)What sort of career are you "allowed" to have in a system where your intellectual property is stolen the minute you think it up and where you have to cope with both "regular" harassment as well as harassment in your mind? All this is in addition to the ordinary stresses of the job -- and not to mention that some jobs require actual mental concentration. How sociable are long-term harassment victims with serious cases of Ongoing Traumatic Stress Disorder? In American society there are also plenty of vicious jerks who, while not Nazis or torturers, are quick to sense perceived weaknesses in people and home in on them. The Nazis can often just wound a person and then throw him or her to the sharks, bleeding. It is natural for humans to think about other people. It is even natural to run a mental simulacrum process to imagine and empathize with other people. Monkey see, monkey do, air guitar, "I was just thinking of you..." etc. The rapist pigs try to turn this against the human beings they torture. Sex is also a natural process, as is farting, masturbation, defecation, burping, spats with people, fantasy, and so forth. The rapist torturers try to turn this against their victims. They constantly attempt to demean their victims. Worrying and anxiety are also normal human emotions. The torturers, though, try to turn all of these human properties against their victims. One technique the Nazi pigs use is to try to reinforce anything you might worry about or feel anxious about. It is like taking a dynamical system and driving it at its natural frequency in order to purposely destroy it. Of course this is not to say the idiots know anything about dynamical systems. If you ever read Lord of the Flies in junior high school you know about the level that these pig idiots operate at, but when they rape your brain to inflict such ridicule and hatefulness it sets up positive feedback processes in the brain that constitute torture. (If I am teaching these idiots anything by this, then you had better watch out because they have already tortured me.) They will purposely injure you and then pick at your scabs if you start to heal. This process also happens because you know damn well you are under surveillance and the pig ridicule squad is there to taunt you. Try not thinking about something you are conditioned with "cattle prods" into knowing will result in harassment. You know the torturers will zap you -- that is why they goad you with triggers at times -- but it is like not thinking of a pink elephant on command. Yins produce yangs, so to speak. Transcending the yins and yangs is hard enough without the torture. The torturers treat your personal, private, internal speech as if it were your public speech. They try to subject you to all the ignorance and "political correctness" and everything else that someone at a podium in a public place might be subjected to. The sadist nanny state is not just concerned with what you say in your own home, they want to regulate what you think inside your head also. That can really cause your "moron anticipator" thought pattern to distract from your normal private thinking, because you cannot even think your private thoughts without knowing they will be "reviewed" for you by rapist morons. The Possibility of Magician-Like Illusions to Deceive VictimsThe technology for thought inference does exist, but it is important to keep in mind the ways in which magician-like deception operations can be applied to a person to make it seem to them that their mind is being read. While some victims' thoughts are read, all of these techniques have likely been tested on nonconsenting American citizens. The classic example is where the "magician" first subliminally "inserts" a thought into a victims brain and then later the magician "reveals" what the person was thinking. By waving his hands and strongly suggesting to the victim that his thoughts are being read, the victim sees the phony "evidence" and tends to believe that is what is happening. The outrage, indignation, and terror responses the victim is feeling will also tend to interfere with his or her reasoning processes. Advanced profiling and prediction, based on standard surveillance techniques, is another possible means for deceiving a person into thinking their mind is being read. While some victims have undoubtedly had such deceptions inflicted on them, the black budget torturers -- before they will admit the true extent of technological advancement -- will likely try to claim this is what was done in all cases. Purposefully setting up the illusion of mind reading on a victim, though, is every bit as despicable and criminal as actually doing it.The setup for the elementary example above can be carried out with only a basic voice-to-skull projection device with the victim in range for some period of time. Suppose you wanted the victim to think about blue violets, for example. You could beam at the victim very quiet suggestions of "blue violet." You could send them a song that they thought just got stuck in their heads. You could use voice cloning technology and try to fake their own voice in their head. Another technique is to transmit a word or phrase that is closely associated with what you want the victim to think about or do, and let their brain's associative memory do the rest. Now, after the subliminal send, the tension and drama build until the sadist magician culminates this particular deception operation against the mark (a.k.a. human being). The magician sends an email to, say, a public mailing list the victim is known to read. In the text of the message the magician works in the phrase "blue violet" -- perhaps combined with a subtle threat. Multiple Victims, Multiple PerpetratorsThe above example is only the most elementary, of course. What if two victims were interacting, how could a pair of them be manipulated? The variations include two nonconsensual victims, or a consensual harasser messing with a nonconsensual victim. There are also witting and unwitting victims; some have figured out parts of what is going on (intended or not) while others have not. Some have been purposely duped into misinterpreting what is going on -- they may think they are psychic, for example. What about wide-field projection devices? If two interacting people are given the same subliminal stimuli, how might they interpret it? If you weren't paying close attention, would you know if you were the sender or the receiver? Especially if the manipulation continued for a long period without your awareness, perhaps even from childhood. When PTSD is purposely induced, the victim is that much more susceptible. Then you can consider the case where there are far more than two victims interacting: a society of would-be slavemasters and those they would hold as slaves. The general situation involves multiple victims and multiple perpetrators, all interacting.There are many, many different scenarios. I even considered writing an academic paper on the topic, something like "Mind Control Games People Play." Suppose you assume a particular set of technologies is available. What logically follows from that? It is like science fiction except that the reality these days is beyond science fiction. The military might call it wargaming. It is amazing the hideous sorts of operations that are possible with only your basic secret video/audio surveillance of an individual. Now assume that a targetable voice projection device exists. What could the people controlling it do in the worst case? What sorts of deceptions could they carry out? What countermeasures could be adopted? When it really does exist and the consequences are so far-reaching, isn't it unconscionable to leave the public in the dark about it? Could a politician resist abusing this secret power? For the purposes of the rest of this essay I will assume our composite victim has been "injected" or implanted somehow with a "brain bug" that transmits tracking information as well as audio and video of the sights, sounds, and internal subvocalized "thoughts" the nonconsenting victim experiences. This is something like an advanced form of the CIA's "Acoustic Kitty" project from the 1960s, where a cat was wired up as a motor-controlled listening device to be used in spying. The difference is many years of technological refinement -- integrated circuits were not even available then, let alone nano-scale devices -- and the obvious difference that a human being is being tortured. I assume that this device can also inject sounds which the victim perceives as if he or she "heard" or "thought" them in internal speech. This is somewhat less control than what some victims report experiencing, but nonetheless is sufficient to illustrate most of the methods. Even if such devices are not available to some particular group, variations of most of the techniques can be created by lower-tech methods like standard surveillance devices and external "zapping" or voice projection devices which are publicly known to exist. The point is not the particular technological implementation, but what the victim experiences. The Realtime Idiot and the AutopigThe term I use for an external voice projected into a victim's mind is the realtime idiot. For an illustration of what the realtime idiots "seem like," consider a secret studio like at a radio station. The "DJs" in this case are the rapists "monitors" who sit and listen to the violated thoughts of the victim. These torturers also have microphones where they can "converse" with the unfortunate victim in realtime. The victim hears these transmitted voices in his or her head. Perhaps the rapists also have a virtual reality computer display of everything the victim is doing at the time, or even a display of exactly what the victim "sees" through his or her eyes. Any thoughts the victim has, the realtime idiots try to pretend it is like a conversation with them. You could not think a rhetorical question to yourself in your own private thoughts without the realtime idiot's comments. You could not pause for a moment of silent mental reflection. They comment on things, they harass, they goad, they distract, they try to issue "commands," they attempt to demean the victims ("Go brush your teeth"). This all while the victim tries to live his or her regular, "ordinary" life and interact in the phony society.At this point I have described the technique whereby Nazi pigs beam words and voices into the mind of the victims in order to harass and torture them. This requires too many low-level Auschwitz guards, though. These dumb sadists may get drunk and start talking, or they may get religion and try to expose their former activities. The need for personnel also limits the number of victims, or "subscribers," who can be controlled by the system. The American answer, of course, is to use technology to automate the process and increase productivity. This results in a device I call the autopig (or the Cameron/Delgado memorial autopig). The autopig at its simplest is just a digital recorder that sends fixed "messages" to the victims at random times. This is very similar to Cameron's psychic driving torture that he inflicted on people coming in for psychiatric health care. I sometimes call these random "pulses" Bergeron pulses after Vonnegut's short story "Harrison Bergeron" (not the movie, which is good but different from the short story). In the story all people were forced to be "equal" by handicapping those with exceptional abilities, and strong thinkers had to wear a device which would periodically emit a loud tone designed to disrupt the their thought stream. Of course an autopig could also be used as a computer-aided torture device so that a single human torturer could switch between victims, secure in knowing that none of them was being left alone in their "private" minds. The Delgado part comes in when the device gets feedback from the victim's brain and sends an "appropriate" message. That is, the sensor system analyzes the brain rape data, an AI-like algorithm decides what sort of response to send to the victim, and then the digital voice simulator constructs it and sends it. Thus each victim has his or her own "electric fence" or something like the invisible fencing they use on dogs but more technologically sophisticated. (You can consider things like stateful autopigs and stateless, or memoryless, autopigs, and so forth. It is basic engineering.) Besides realtime idiots and autopigs, there is something I call a Delgado button. A Delgado button is a button the harassers can press and which stimulates some part of the brain. There may be many Delgado buttons, for example, and the harassers learn what each one does empirically by observing the victims. To the victim a Delgado button would just feel like some sensation, experience, or emotion came over them all of a sudden. It might occur at a particularly inappropriate time, for example. It might also serve as a distraction when the pigs wanted to stop some particular thought train you were having. It might be difficult to notice; some subjects in published research would rationalize such induced behaviors and say that they just decided to do whatever behavior the buttons evoked. A Delgado button also need not literally be a button and a brain electrode, it could also be something like a microwave beam at a particular frequency and with a particular modulation aimed at a person. Metaphorically there can also be conditioned "software" Delgado buttons in addition to the hardware wired-in electrode buttons. Data Analysis Under TortureNow that I have described the basic mind control operation, in this section I consider the problem of data analysis for a victim of such crimes. Don't blame the victims; try to understand the hideous position they were thrown into and which they in no way got to choose. Naive science-dude has probably not spent 5 minutes considering what victims are forced to agonize over for years. The situation is closer to game theory with a malicious "opponent" rather than to the usual study of natural science, where natural phenomena are considered to be repeatable (or at least indifferent).The victims must rely mostly on their own sensations and introspection; that is just the nature of this sort of advanced, secret torture. This is not to say that evidence of the "ordinary" sorts of harassment should not be collected, or that a breakthrough will not occur and someone will learn how to detect whatever signals or devices are used to inflict the mind control torture and make it available to the victims. The first challenge for the victim, though, is just to figure out what is really going on. Many do not even have the language to describe what is happening to them. They have to see beyond the stagecraft ("tradecraft") of the Nazi technical illusionists. The victims need to live their lives each day with whatever mental firewall countermeasures they can adopt in their minds. Beyond this they can gather evidence to convince other people or for a lawsuit. They will discover, though, that for the time being the court system, like the psychiatric system, is part of the problem. How many times does someone have to beam a clearly external voice into your head before you have to question all your thoughts? Not too many times, once really. Some victims of this "one-shot" voice projection mind control may still suffer for years. When will you believe they are not reading your thoughts or that they are not trying to manipulate you? When the truth commission reveals the crimes? No, you will never believe them again once you know how the pigs operate. Most victims suffer from far more than just one voice projection experience, though. Internal and External Thoughts and Sensory InputsInside the mind, the torture victims really are human beings just like everyone else (even though they are treated worse than anyone would treat a dog). They see with their eyes, hear with their ears, etc., have internal dialogs thinking about things, sparks of intuition, and all the usual features of the human mind. As mentioned earlier, these are the processes the mind controllers attempt to hijack. For the victims we can consider that their thoughts fall into three categories: internals, conditioned internals, and externals.An internal is a normal, natural thought grounded in external sensory input that the person consensually engages in. The usual thought model that most people have the luxury of believing is that all of their interactions are consensual and that their private thoughts are actually private and not tampered with. That is, they only experience internals. An external is a nonconsensual input, like Cameron's psychic driving where a person is strapped down and forced to listen to manipulative recording loops. In the modern sense, the externals are the voices projected into a person's mind from an external source. (You can theoretically have consensual externals, even of this sort, but the victims certainly never saw a consent form and you'd be a fool to consent to having the pigs the victims are familiar with have anything to do with your mind.) The signal from a programmed autopig chip in the head would also count as an external. An external could also be an email from a Nazi that is based on mind-raped data. Any normally consensual interaction becomes an external when mind-raped data or psychological triggers are purposely embedded there. A conditioned internal, in the sense being discussed here, is an internal thought process that is a direct result of the torture by externals. The mental "fruit of the poisoned tree," so to speak. After a week or so of having "you are a good marine" drilled into your head from nonconsensual externals, then when the machine is turned off there will likely still be the tendency to hear the phrase. (Besides whatever other damage such harassment causes.) This is especially true if the conditioning was specifically focused on certain stimuli -- though random stimuli also become conditioned in the same way that a bell ring is associated to the bowl of food by the salivating dog. A similar-sounding phrase, for example, can serve as a trigger for a conditioned internal. Conditioning during trauma is also strong and long-lasting and can bring back vivid feelings of the original torture experience. The manipulators can probably get some unwitting victims to march around their own homes like controlled robots. People's sensitivity to what is internal or external "in their head" would vary according to the person. Age, length of abuse, and the particular technology and techniques used would also influence who becomes "witting nonconsensual." Perhaps this is a part of what determines who they harass and try to "break" and who they secretly control. Those susceptible to hypnosis might be especially vulnerable, and some victims may be influenced only while they sleep. (Is it terrorism to call for blowing up a Nazi torture center that "doesn't exist"?) The ProtocolA way to verify that a signal is purely external is via the protocol. This protocol assumes you have a cooperative person on the other end of the external channel you wish to authenticate. In practice, what you learn is that if there is such an external channel you do not have a "friendly witting" on the other end. (And victims know from long experience that there is such an external channel.) That is, the protocol is a way that a "friendly witting" could authenticate to you the existence of an information channel that supposedly "doesn't exist."If you have visual, auditory, or tactile contact with a person the protocol is easy. (It is better if they cannot see or hear you, since that constitutes another, uncontrolled data path.) Suppose you can hear a person talking. Then the protocol is to think to yourself something like, "say 4533." You may wish to choose something else they could say without attracting attention, if that is a problem, but be sure it is something which is very unlikely without a mental send. Count, say, five seconds for a response. Either they hear your thoughts or not, and they either respond or not. In this case the channel is specific to a person and may not exist or the person may not be a "friendly." For visual contact the situation is similar, you can think something like, "hold up three fingers." Notice that this protocol also works for something like listening to a realtime broadcast such as radio. A similar protocol works for written media, think "write the number 6423" and email it to me or put it in your newspaper column. Note, though, that in all cases there may still be a hidden "man in the middle." You can actually verify a pure external send and receive without visual, auditory, or tactile contact. Just the "mental" contact. This applies to anyone and everyone who can hear your thoughts and send a reply. It requires that you have a calculator, and a cooperative person with a calculator on the other end of the channel. The protocol is, "What is the cosine of 1999?" The first four digits after the decimal, in radians, one at a time. If the pigs cannot send that data they are either retarded or engaging in a conspiracy. There are a couple of other possibilities, including pure internals, but the point is to have a cryptographic authentication challenge to verify a pure external send and receive. Anyone can punch the buttons 1, 9, 9, 9, cos on a calculator. I do not know the answer, but I can check it easily. [You should change the number 1999 to something else for your own protocol, since you want to be able to conclude a pure external read and send. The number is something you only think "to yourself," and choose a new challenge number each time you check a response with a calculator.] They never send valid four-digit numeric data, let alone the correct answer. They do send numerics, though, and could presumably program the answer into the autopig. And they get sloppy sometimes and you get a good strong piece of data that indicates external reads and sends, even though they do not send the protocol. This is one reason such a protocol is useful: It illustrates what the ideal data would look like for a remote read and send, and can help clarify more ambiguous situations. But keep in mind possible magician-like deceptions as were mentioned earlier. The Calibration ProblemIn evaluating uncertain data in the real world, including that from hostile sources, it is important to calibrate the expected level of background noise. If you are reading the torture between the lines, you also need to keep your head and not go off on too much unconnected symbolism. Keep this in mind when reading items that truly could not possibly relate to you or your situation. This gives you an idea of the basic background level for symbols, etc., to appear. Keep a threshold and discard any questionable data. The good data points tend to be frequent enough, and at some point even they do not tell you much you do not already know.As an example, suppose you cursed the pigs, just in your head, sometimes. If you get them angry they sometimes screw up. Say you were taunting them by asking them whether they picked up your thoughts in Niger (as an random example of a far-off place). By the way, you can taunt them all you want in your head, since it is only you and the Nazis there. Likewise, curse the pigs that bug your house all you want. They just do not seem to understand that if they reveal anything they know about your private mentation or private conversations in your home they cannot call you crazy. It would be like entering the FBI tapes of Martin Luther King saying the FBI was out to get him as evidence that he was paranoid. "The voice in my head said I was crazy." Back to the Niger example, suppose you then get email from someone claiming to be a victim, who has a name very similar to yours, and who claims that he went to Niger and could not escape the harassment. That seems pretty unlikely for a coincidence. Then the question is, is the person a witting or unwitting harassment agent, i.e., is it another victim manipulated into harassing you or is it a cointelpro agent? How many people have been to Niger? Many victims are understandably afraid to talk about such experiences, though. Reasoning Under UncertaintyOne thing that the mind controllers do -- and which manipulators and propagandists have done for all time -- is to exploit weaknesses in human reasoning. The brain is a fantastic, beautiful organ of the human body; no human being on the earth should ever be tortured. But humans also tend to have some weaknesses in evaluating data compared to, say, a mathematical algorithm. One difficulty lies in dealing with uncertainty. The mind control victim is literally overwhelmed with uncertainty and must sort things out as best as he or she can. The victim has to consider every weird thing that has ever happened to him or her, whether it is related, and knowing that the mind rapists will see this thought process and try to reinforce any misconceptions. Another difficulty is dealing with distractions, especially when they come in on a hostile "channel" that the brain was never meant to be accessed on. Proportionality and scale are another difficulty, and people tend to think binary rather than continuous, and one-dimensional rather than multi-dimensional. People often have a tendency toward superstitious thinking. Finally, in a social sense, people are very bad at dealing with big lies, i.e., conspiracies of liars.Understand aggregate statistics. You can sometimes reason better with them. As an example, you know that there are some people in the world you can trust; you just don't know exactly which ones they are. You can often estimate aggregate statistics better, since if you get one wrong here or there it all averages out. Suppose you estimate, based on a great deal of data, that posters on some mailing list are, say, 40% agents and provocateurs, 35% real victims and activists, 15% who probably consider themselves scientific, nonsuperstitious thinkers looking for the truth, and another 10% who are unclassifiable. There are some who you are sure enough about to not worry with percentages, but in general any particular person on that list is "suspect." Nonetheless, the list can still function as a way to reach and connect the 35% of mind control victims and activists. It may also serve as a way to convince and educate some of the actual open-minded decent people who are not mind control victims. Another use of aggregate statistics is to reason from historical records. We know that there are thousands of mind control victims in the population, at the least. We just do not know which particular people claiming to be victims are the actual victims (or which still unwitting people were/are victims). Never forget the humanity of the real human beings involved in the statistics, though. The Asymmetry of DignityYou are a human being with unalienable human rights. Unalienable means that they cannot be taken away. They can be violated, infringed, ignored, and even legislated away, but the acts of a tyrant do not change the fact that you are a human being with unalienable human rights. This means that the tyrant is always a tyrant, and remains a tyrant, to meet the fate of tyrants. The same holds for the lackeys and collaborators of tyrants. This is a fundamental asymmetry between the citizen and the tyrant.Torture demeans the torturer. The dignity of the torture victim cannot be taken away by the torturer, but the act of torture destroys the dignity of the torturer. This is not enough punishment for such hideous crimes, but gives cause to pity the torturer even as you work to hang the pig. Let me explain about what I mean about justice for the victims of these treasonous Nazis, who commit crimes against their fellow American citizens in peacetime which would be war crimes even against an enemy in warfare. Under a legitimate government such people would receive life sentences in a humane prison system. That would be my preference, but the United States currently has neither. So when I talk about hanging the pigs I am referring to whatever justice-type processes can be set into motion. That was the subject of Part II. Get the right ones. We will not forget, and when these pigs are 75 years old they are still Nazi pigs and still serve the rest of their worthless lives in a humane prison cell if such exists. The legitimate government treats mind control torture like the true crime it is, even when government agents are involved in committing the crimes. You have absolute free mentation in your brain and mind. Your freedom of thought is unalienable. The Nazi Pig TheoremThe adjective, "Auschwitz-level," to describe these crimes, is not hyperbole. If you do not feel like you need to vomit, you probably do not really understand the full sickness of mind control crimes. Gordon Thomas wrote in the introduction to his book Journey Into Madness: The True Story of CIA Mind Control and Medical Abuse: "In working on this book I have had to come to terms with my own emotions -- disbelief, bewilderment, disgust, and anger and, more than once in the early stages, a feeling that the subject was simply too evil to cope with. Nothing I had researched before could have prepared me for the dark reality of doctors who set out to deliberately destroy minds and bodies they were trained to heal." Torturers can never blame their victims, though they invariably try. These torturers are the sorts of people who will repeatedly hit a bound and gagged victim with a stick and then try to claim the victim caused it. They'll steal from you and then complain about the property they stole; they'll rape you and sneer at the quality of the "sex."This
brings me to what I refer to as the Nazi Pig Theorem (NPT).
Strictly speaking it is a metaphorical axiom, but it can be very
useful to the torture victim. It basically asserts that if
you act like Mengele then you are a Nazi pig. Then there are
a few obvious conclusions that are also part of the "theorem."
Isn't that obvious? Don't you believe it? Then remember it and act like you know it. NPT is as sharp as a razor. The contrapositive of NPT is also useful: If they are not Nazi pigs then they are not raping your brain. So you can think anything about anyone; it's just you and the Nazis in your mind, and their opinions do not matter at all. If you have a passing thought about someone and the Nazis try to harass you with it or make you feel guilty about it, it does not matter. The Nazi pigs' opinions do not matter (unless they somehow help to get the pigs hanged). If you think some thought about someone who really is raping your brain, then you have some worse things to think about that Nazi piece of human garbage than what floated through your brain originally. One use of the Nazi Pig Theorem is to try to go on with ordinary life even as you are being tortured and you know the true, evil nature of the society you are living in. Spend some time each day working for justice in the physical world, and the rest of the time try to ignore the Nazi pigs and get on with your life as best as you can. My philosophy is basically to wish people well, and any differences I have had with people are all water under the bridge after not too long. But atrocities never, ever pass under the bridge. The victims never forget, and never should forget. Of course any victim is free to choose to forgive his or her torturers, but for torturers to lecture their victims about forgiveness is the "Christianity" of the oppressor. Forgiveness also does not preclude justice. The unfortunate reality is that when dealing with anyone, they are either a Nazi or a non-Nazi. Torture makes it that clear. This is the top node of the decision tree for the torture victim, and it is a stark split. The following diagram illustrates the split: 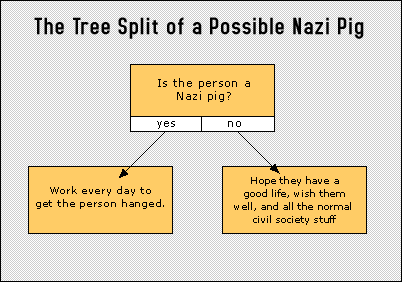
That is clear enough. Of course the difficult part is that you do not know exactly who is a Nazi pig and who is not. So you might start off with a reasonable benefit of the doubt and collect evidence from there to update your current assumptions. But how do you deal with someone you think has a 10% chance of being a Nazi pig? How do you deal with someone you think has an 80% chance of being a Nazi pig? That is your own utility/decision function and it is not easy. People have to make decisions based on imperfect information all the time, but this purposefully inflicted torture pushes it past what people are accustomed to have to deal with in ordinary situations. Nonetheless, the government is accountable for the aggregate situation where torture occurs regularly and systematically in American society. The NPT is your firewall. As a corollary, the external firewall theorem states that you do not care in the slightest bit what Mengele thinks. Analyze the external incomings for nature and source, as well as for other evidence if you choose to, and then send them straight to your mental /dev/null. Then work each day to get the pigs hanged in the real world, in the best way you can figure to do it (see Part II). There is also an internal firewall theorem: Your brain is your own to think whatever you want with. Simply invoke IFT and think about something entirely different if you are thinking something that you don't want to be thinking about. Train yourself toward that, at any rate. Some Suggestions for Thinking about the HarassmentThe way to think of a nonconsensual external is as an advanced cattle prod that can be modulated in various ways to cause you pain. The modulation happens to be with words or clicks, but that is secondary. It is a modulated cattle prod. Notice it and try to get a feel for the nature and source of the signal. Where does it seem to be coming from? What is the quality of the signal? Later you can analyze the psyop sentence the pigs modulated onto the cattle prod signal if you feel like it. (This may reveal more about them than about you; the modulation is based on "you" reflected off of their filthy Nazi distorting mirror -- with their intention being to cause you harm.) You might keep a rough histogram count on the autopig phrases, for example. Does the signal ever have a foreign accent or speak a foreign language? Probably not. But basically understand that the Nazi pigs are complete, pathological liars. If they flatter you one second they'll kick you in the head three beats later, you can almost count on it. Pathological liars only tell the nominal truth as part of a larger lie, and the purpose is to destroy your mental well-being and your life.Source before semantics (signal before semantics). The source is where the signal comes from, both the "person" sending it and the sensory input method by which you receive it. The semantics is the meaning of the signal: it is the interpretation of the signal and its modulation. For example, the semantics of a signal will often be its interpretation as an English sentence. If the signal comes in on a rape channel, do not even give it a semantics except perhaps as part of an evidence-gathering process. It is just a sensation you feel from the external cattle prod. The presence of the nonconsensual external signal itself is torture and is the only real information, since the modulation is by pathological liars whose intention is to cause you harm. Don't debate the autopig (or the realtime idiot). Even if it's easy. (Unless you feel like it.) They hate it when you ignore them. Go on with your ordinary life, meeting people, etc., and especially speaking out and working for justice in the real world. You can only really ignore them when you know what is going on, though. Some of the people who they march around their own homes like robots probably think they are just ignoring it. There is a big difference between an experienced victim deciding to ignore future signals and some well-meaning advice-giver who has never been tortured telling you to "just ignore it." If it is indistinguishable from an autopig, treat it as if it were an autopig. With some basic voice-recognition type software applied to raped subvocalized thoughts, I could write an AI-like program that sounded just like the repetitive, simple-patterned Nazi pigs I am familiar with. In this sense, the realtime idiots do not even pass the Turing test. Actual people (who are not torturers) have names, they do not repeat things endlessly, they think things other than harassing you and commenting on your thoughts, and they can push a few calculator buttons. For instance, why do you never hear someone driving their car down the street thinking "use a turn signal, you asshole"? Don't explain your thinking to the Nazi pigs, it is better if they misunderstand what they rape from you. By default you are only ever thinking to yourself. Work toward the rapid extinction of the Nazi conditioning imposed on you, at least as rapidly as you can manage. Try to extinguish your conditioned responses and replace them with only an awareness of the triggering sensation. Some are random events acting as triggers, while others are purposely inflicted. It may help to write about what you experience or keep a journal. There are pros and cons to this, though, since the pigs will have access to what you write also. It might provide them with feedback to help them torture you or others. If you complain about something they will almost surely start doing it to you more. You have to weigh whether writing about it helps you to deal with it, like when you can share it with other people or when you see how stupid it really looks when written out. Stupidity is no barrier to the torturers, in fact it is part of the torture. For example, if you make a self-deprecating joke it will not be long before the pigs are goading you with the subject of that joke for real. Of course much of the torture is never anything clever the torturers do, but your own knowledge that these people who do not even know you nonetheless hate you enough to violate your mind and then go to a great deal of effort to try to inflict serious harm on you -- often seemingly for their own entertainment. Try tuning out the pigs like you might cure yourself of hiccups. It might work, or at least help you train yourself to ignore the pigs. Notice the nature and source of the signals, the mental gnats meant to annoy you. Parasitic mind fleas. If you think like the monkey, you'll be as dumb as the monkey. If you watch that TV too much you'll be as dumb as the morons on it. They will entertain you right into digging your own grave. How Can a Society I Detest Defile Me?How do you deal with a secrecy-bred society of dumb-as-cows "innocent" people, Nazi pigs, and victims? Or the collaborators, apologists, and profiteers? What about the people who idiotically ask, "Why are you ongoing torture victims so obsessed with your torture (and human rights, etc.)?" The social system where no one can talk about the elephant in the living room, even though many people know at least that something is there. Did people not get born with tongues to speak with? Or is this a conspiracy of idiots and cowards? What the hell is wrong with these people? What kind of people complacently live in a society where torture regularly and systematically occurs, pretending it doesn't? Is it still that old pig slaver mentality, or the ability to look away from such abominations as an everyday thing? For centuries it was forbidden to teach slaves basic skills like reading. Is it better if you can read but only have access to lies?Every day for the mind control victims, it is like the rape victim who has to go out and interact in the society where her rapist is still at large. The difference is that there is a whole conspiracy of rapists and they rape the victims each and every day. So perhaps it is closer to what were euphemistically called "comfort girls." How do you think it feels to wake up with a pig in your head? Is that the only alternative to being dumb as a cow and wearing a gag in this society? The "consensus reality" of the average citizen is far, far from the real truth on the ground. Americans are the best liars and biggest hypocrites on the planet. They will probably even be flattered by that description. They love being number one, after all. Hypocrisy is like lies, in the sense that there is ordinary hypocrisy and there is big hypocrisy. If you credibly call an American a big-sense hypocrite they will often start spewing propaganda that celebrates ordinary, everyday hypocrisy like not telling someone their new haircut looks bad. Americans want to be both peepers and prudes, they want to rig the game and call it free enterprise, and they want to be known for freedom and liberty regardless of any domestic atrocities they commit. You can never un-torture someone. If
people are capable of outrage there will be far fewer outrages.
How dare those pigs do that to anybody. -- If it's not
useful or enjoyable or necessary, it's a worthless thought. Truly internal,
self-mind control is a good thing; No nens follow
from nonconsensual externals, Ah, how sad
it is, Auschwitz in the springtime... --
Part I - Motives for Mind Control | Part II - Resisting the Mind Control State | Part III - Mental Firewalls |
|
|
|